Home Our blog Passwordless authentication in Azure AD - Microsoft Authenticator, FIDO2 and Code Match for MFA
Passwordless authentication in Azure AD - Microsoft Authenticator, FIDO2 and Code Match for MFA
05/09/21
Pavel Otych
Passwordless authentication is a topic that Microsoft has been promoting for some time. In this post, we will look at passwordless authentication in more detail and summarize some practical experience.
What is passwordless authentication?
Let's start from the basics - what exactly is passwordless authentication? As can be understood from the term, it is a form of authentication in which the user does not use his password, but logs in in a different way. In the world of Microsoft and Azure AD, the available methods are:
- Windows Hello in Windows 10
- Microsoft Authenticator iOS/Android application
- FIDO2 security key
How does such a login work? In all the above cases, it is a login that also meets the requirements for multifactor authentication - a combination of something the user knows and something the user owns. A typical combination is a PIN and a managed device (for example, Windows Hello without a camera) and a combination of biometric authentication, code, and another managed device (this is the case with using Microsoft Authenticator on a mobile phone). Therefore, the user must verify and confirm that he is currently controlling the device on which the login attempt without a password is approved, or that he is using the FIDO2 key. This guarantees the safety of the entire process.
Passwordless authentication aims to prevent someone unauthorized any possibility of password eavesdropping. For example, if a user logs in to a company email in an Internet café, they will confirm the login on their managed company phone, or use the FIDO2 key. He does not enter the password into the computer in the café at all and there is no danger that someone will find out or eavesdrop on the password.
Microsoft Authenticator
So how do you use Microsoft Authenticator for passwordless authentication? On the Azure AD side, a few requirements must be met, namely to enable combined security information registration experience (the process is a single click for old tenants, for new ones the feature is already enabled by default) and then to enable passwordless notifications to Microsoft Authenticator (enabled by default).
On the user's side, it is necessary to meet the condition that the device is registered in Azure AD. Subsequently, the user can enable passwordless authentication for his account in Microsoft Authenticator.
In practice, the login takes place in such a way that after entering the username into the browser, the user is referred to a two-digit code confirmation instead of a password, which appears in Microsoft Authenticator after unlocking the device and biometric confirmation. After confirmation on the phone, the user is logged in and did not have to use the password at all.
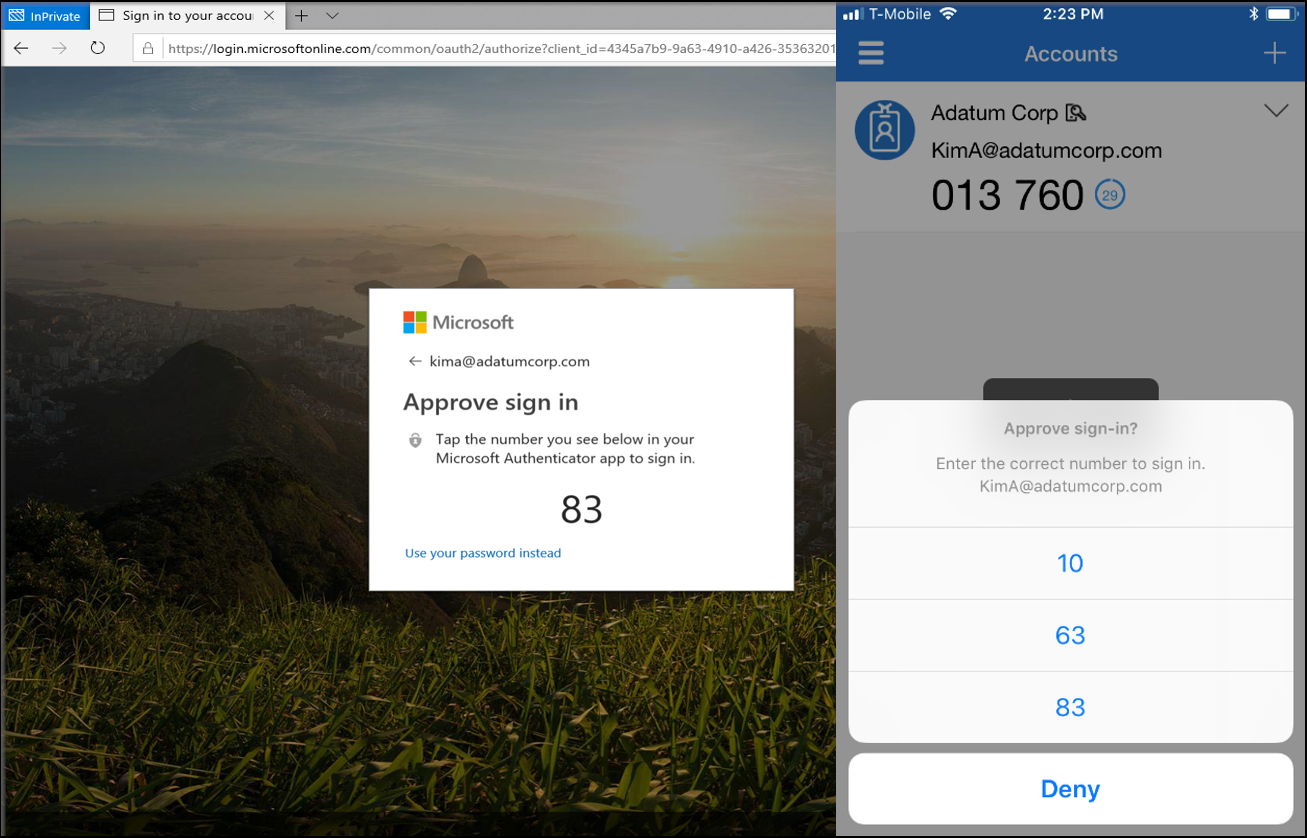
What are the pitfalls in practice?
A mobile phone with Microsoft Authenticator must be registered in Azure AD, which can cause complications for those with multiple accounts. Both Android and iOS can be registered in Azure AD only once, so we can turn on passwordless authentication for only one account.
The biggest challenge for administrators is that enabling passwordless authentication in Microsoft Authenticator cannot be deployed automatically without the user going through the registration process in the application. Although the registration process is a matter of a few steps, it is still something that can cause problems for an ordinary office worker. The administrator must be prepared to create a pictorial manual with a description of the process. In Azure AD, regural MFA push notifications can be disabled in the settings and we can force users to register for paswordless authentication, but unfortunately we do not yet have the option to skip the whole process and automatically turn on passwordless authentication globally for all users.
FIDO2 security keys
One option for passwordless authentication is to use FIDO2 security keys. These are simply put standardized security keys (usually plugged into USB, but can also use NFC), which act as a replacement for passwords. The use of the key is usually protected by a PIN and, depending on the specific product, also by other mechanisms (either by a touching the key, or preferably by a fingerprint). In the case of using a key without biometrics, it is theoretically possible to say that security is lower than when using Microsoft Authenticator, because to use the key you only need to know the short PIN with which the key is protected. Of course, this is a matter of choice and in Azure AD we have the option to limit the use to keys with a specific AAGUID (pretty much a product number). So if we bulk purchase keys with biometric verification, we can guarantee that another type of key cannot be used.
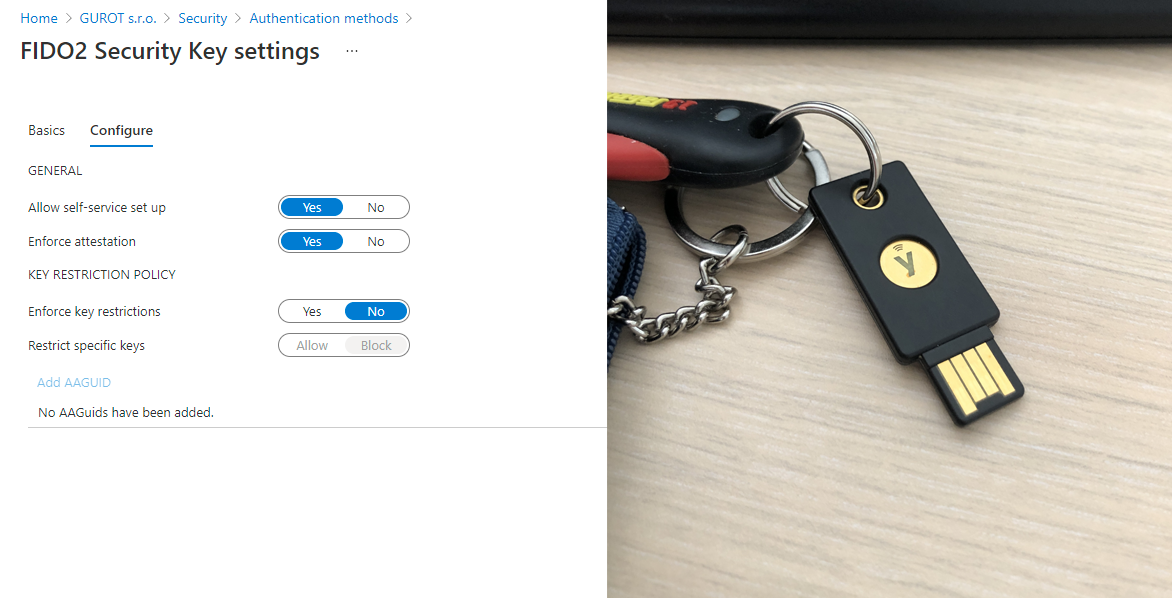
We can also use the FIDO 2 security key to log in to Windows 10. Unfortunately, the snag is that only for logging in and not to elevate rights in the UAC dialog on the station. This is a great pity, because this is exactly the use I can imagine in small companies - a user has a problem on the station, maybe he needs to install something, the admin comes to him, inserts the FIDO2 security key and does what is needed (now let's not take into account that in an ideal world, each station has a unique local admin account, the reality is often different). Unfortunately, this is not possible.
Logging in to shared stations seems to be the ideal use of FIDO2 security keys. FIDO2 security keys work without problems for logging in to Windows 10 and it is something that has proved its worth in practice with many clients (in theory it is possible to log in to Windows 10 via Microsoft Authenticator, but in practice it is not completely ideal).
Unfortunately, at present, administrators have no choice but to rely on the user to go through the registration process and set the FIDO2 security key themselves. It's not drastically complicated, but again (as with Microsoft Authenticator), be prepared for the need to create pictorial tutorials and descriptions so that an average office worker can complete the process.
Code Match for MFA
From the above, it is clear that the current biggest obstacle to the deployment of passwordless authentication is the inability to automate the entire process for users so that they do not have to set anything. We hope for better times here. Some time ago, the App Lock function was added to the Microsoft Authenticator, which is turned on by default and which requires a PIN or biometric authentication when opening the application. This may seem unnecessary at first glance, as most managed devices already require PIN / biometrics to unlock, and passwordless authentication also needs to be biometrically verified. But Microsoft knows where he's going with this step.
Code Match for MFA is basically an "old" MFA authentication enriched with a passwordless process. Instead of entering the password and then verifying with the second factor, MFA can be used as passwordless authentication in the same way that passwordless works in Microsoft Authenticator now, but without the user having to turn on the feature, register the device in Azure AD and set anything.
So far, we are far from practical deployment, the feature is available for personal Microsoft accounts, was available for a while in Azure AD as a preview, and then removed for further completion. According to the current roadmap, it should be available by the end of 2021. For practical use, it is still necessary to complete the management of the above-mentioned App Lock (currently not possible to manage globally) and this management will have to take place via a channel other than MAM / MDM so that the user could also use unregistered devices and at the same time there was a guarantee of PIN or biometric verification.
We'll see what Microsoft comes up with and when this feature will be available in Azure AD. When that happens, I think there will be an opportunity for a truly mass extension of passwordless authentication, where the user does not have to set anything and everything is in the hands of administrators. Of course, the question is how everything will turn out, one cannot be sure of anything at Microsoft, and as long as the function is not publicly available, we can only hope.
Conclusion
Passwordless authentication is definitely suitable for anyone who wants to increase the security of their accounts. Password theft is still the most common way to hack into company accounts, and any feature that makes it difficult for attackers is appropriate. Using passwordless authentication in Azure AD is easy, but it can be difficult for regular office workers to activate. Administrators currently do not have options for setting up passwordless authentication globally for their users, but this could change in the future with Code Match for MFA.
